| Protocol stacks | |||||||||||||
Sometimes it is easy to forget about the amount of work required to send a single packet of data over the network. There are many different tasks which need to be carried out. How will the packet get there? How will the packet be formatted? What will the packet contain? Does the packet need to arrive in a specific order? What happens when a error is introduced during transmission? Due to all of the work which needs to be done it is not practical to place all of this work into a single protocol. As such a number of protocols are chained together known as a protocol stack. Protocol stacks have many advantages -
TCP/IP protocol stack, shown below, is a prime example of why protocol stacks work well. Each layer, apart from the bottom layer, there is a choice of which protocol to use. Each choice provides a different service and as such will have different properties for the packet being sent. For example the UDP protocol is a "fire and forget" technology. It provides no error detection and provides no guarantee on the order of packets. If the packet fails to arrive at the destination then this is just too bad. This may not seem desirable but on the positive side UDP is much faster than TCP. This would be ideal for video transmission where speed is more important that accuracy however when sending a file over the network even one byte out of place could cause the file to be corrupted.
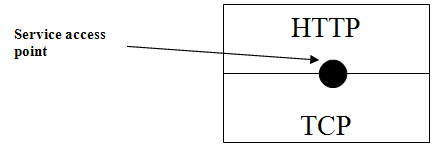
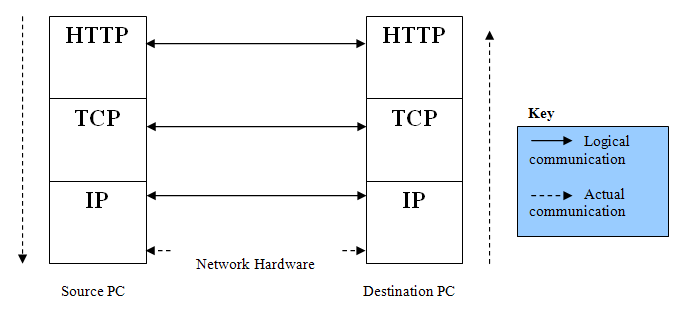
Layer 3 has a large number of choices. This is sometimes referred to as the presentation or application layer. Essentially the protocols used here are very specific to applications. For example HTTP (Hyper text transfer protocol) is used to transport WebPages. FTP (file transfer protocol) is used to send simple files over a network. Depending on the application which is running will depend on the transfer protocol used at layer 3. Having this choice, of layer 3 protocols, means that it is very easy to add new protocols without having to change any of the existing structure. This is made possible due to a common interface being made available from layer 3 to layer 2. So HTTP and FTP will create a packet differently but will set it up in such a way that any of the layer 2 protocols will understand. Each protocol will offer different services but will always format packets so they can be understood by the other layers. The service access point (SAP) is where the protocols will communicate with each other. This access point will be made generic so that any of the protocols can be swapped out without effecting the other protocol. That way it is the applications choice of what services it requires without having to worry about tailoring the data for a specific protocol. It is important to note that protocols at both sides of the network must match otherwise the packet will not be understood. The diagram below tries to explain this. The logical communication lines show how each protocol views the communication. Each protocol considers that it communicates with its counterpart directly on the destination machine. This is why there is a logical link between them. However what actually happens is that information is passed down the protocols and placed on the network hardware which transports it. At the destination the packet is passed back up the protocol stack. This is actual path that a packet will travel and is denoted by the dashed line. The logical communication is important as it directly referees to the services offered by that particular protocol. For example TCP offers error detection and is responsible for adding the CRC checksum at the source then checking it at the destination. At no point will this responsibility fall to any other protocol. The checksum which is added is only intended to be viewed by the TCP protocol. This is why each protocol effectively is communicating directly with its counter part on the other PC.
|
|||||||||||||

| Links |
| Protocols |
 Custom Search
Custom Search